Latest from Building Automation
New HVACR Products: March 2025
Crete United to Partner with ProStar Energy Solution
Modular Construction Still Gaining Ground
ASHRAE 90.1: Charting the Path to Net Zero Buildings
New HVACR Products: February 2024
AHR Sessions: Our Collection of Field Reports
HPAC 2024: Our February Quiz!
Can You Protect Your BAS Networks From Hackers?
The security of building-automation systems is a hot topic in our industry. Security professionals are analyzing and discussing the pitfalls presented by hackers. Even Hollywood has taken notice: Several films have explored the topic of unauthorized control of building-control systems. Can you secure your networks? The true answer is, “It depends.”
Let’s look at the issue.
What can unauthorized users do? Why would they want access?
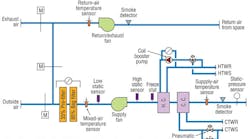
Most building-automation systems (BAS) monitor and control the HVAC systems and, in some cases, the lighting systems. A commonly voiced concern suggests a person could access the system and adjust or turn off equipment. The opportunity of someone hacking into the BAS and doing something other than nuisance type issues is minimal. That’s not to say that the hacker could not cause various comfort problems, just that the benefit to the hacker would be minimal.
Often we cannot determine the “why” of why someone does what they do, but anticipating their intent can help avert an intrusion. Most BAS systems are designed to limit remote catastrophic-control modulations. An example of a catastrophic-control modulation would be closing the main air dampers on an air handling unit, overriding the safeties, and running the fan up to 100 percent, causing the ductwork to explode or the motor to burn up. Most systems have hard-wired safeties that shut down equipment in such a scenario. These hard wired safeties are not controlled by the BAS and cannot be overridden remotely.
How else could unauthorized users access the systems?
We have conducted many vulnerability assessments to evaluate the security of unauthorized access of clients’ buildings and systems, and have found hacking and accessing BAS systems to be of low vulnerability compared to other intrusions. An example of some other intrusions are as follows:
• Most data center or separate cooling systems exterior to the buildings have disconnects that are not locked, and to which anyone could walk up and turn off. Someone could walk up, turn off the equipment, and walk away. There are no cameras on this equipment so finding this person would be difficult.
• Many MER rooms and electrical closets are not locked so someone could open the door, throw the breakers and walk away.
For buildings with a BAS, a hacking incident can be traced and the event is documented.
Are there other ways unauthorized users could access the network?
Yes, here are some examples:
• Most manufacturers have global default usernames and passwords so their technicians can access any of their systems in the field. This is a single username and password that gives people access to BAS systems from a specific manufacturer. Each manufacturer has one of these to troubleshoot systems remotely.
• Usernames and passwords of facility operators can be stolen. Often, these username and passwords are printed and posted near the front-end computer for easy access. Usernames and passwords are often shared. Studies have shown 70 percent of systems have a simple username and password such as JohnSmith12345.
• Someone could steal a laptop or interface device that has all the saved usernames and passwords saved on that device.
Six Steps to Limit System Vulnerability
Knowing this information, how can we make these systems less vulnerable?
1. Design your BAS to limit catastrophic modulation and ensure all systems have hard-wired safeties to prevent the equipment from being operated in conditions which will result in damage to the equipment, fire, or explosion. Examples of protective safeties or relays are high total pressure, low water, low water flow, high static pressure, valve and damper end switches, vibration switches, current switches, and fire and smoke detectors.
2. Design your BAS so that the system can only adjust and modulate systems and equipment. Individual devices should be controlled locally by the equipment controllers. Such a case would be a chiller: let the chiller control the compressors and only allow on/off and setpoint adjustments while the system provides alarm interfaces.
3. Be alert, be aware, be proactive. Look at ways you could cause problems if you could access your building systems. Walk around your facility and identify unlocked doors and equipment disconnects without padlocks or fence enclosures. Lock all mechanical and electrical rooms. Enclose exterior equipment in security fencing. Limit access to roofs and courtyards. Investigate access to air intakes. Can chiller or boiler controls be accessed directly without a password? All BAS hardware should be installed in a locked enclosure with the keys properly secured.
4. Limit users and increase security for password access. Identify if the system can be accessed directly from connection to the BAS panel without a password. Chiller and boiler controls should not be accessed directly. Instead, manage access to these controls via passwords. Change all your current usernames and passwords on regular intervals no less than once per year. Provide new usernames and passwords to only those people who need access. Set system access authority for all users. Very few staff and/or support contractors should be given full administration authority. Senior operating staff can be given a medium access, but most technicians and end-users should have a low priority level.
Institute username and password standardization. Usernames should not be email addresses or people’s names, but separate names with capitals, numbers, and letters. Passwords should be “hard” which means they should be of eight characters or more and include multiple types of characters. Eliminate any default global administrator passwords. Inventory all devices that have direct access capabilities.
5. Harden your network. Separate the BAS network from other networks by compartmentalizing. Create a virtual local-area network (VLAN) that dedicates network infrastructure (switch ports, routers, cabling, etc.) specifically to your BAS devices. Install BAS networks firewall/routers for all external communication links with the Internet and end-user business networks. Program the firewall to dedicate specific ports required for data transfer with external application programs and for end-user browsing of BAS data presented in a Web-based format. Limit the number of permanent BAS workstations. Locate all such workstations in rooms that are frequently supervised and monitored. Never install a workstation in a mechanical equipment room, electrical closet or other area that is isolated and remote. Ensure that all workstations are updated with the latest anti-virus and security software, in a similar fashion to end user personal computers and laptops. For very large BAS networks with multiple domains, install network security and management software on your network to identify, alarm, and correct malicious programs or viruses and keep these current and up to date.
6. Consider a vulnerability assessment for your building, system or network. Do not limit this assessment to computer system access. Each building or system will have different concerns or risks associated with them.
Realistically, it will not be impossible for hackers to access a system because authorized users need user-friendly access to the system. Being user-friendly is a tight line that you need to balance. Remember, you don’t need to make your system impossible to hack; you just need to make it harder to hack than other opportunities. Most perpetrators are looking for an easy target. If you work to take yourself out of that category, you will avert most instances.
J. Christopher Larry PE, CXA, CEM, CEP, CIPE, LEED AP, is the director of energy engineering for exp, Richmond, VA. He has spent more than 25 years working to minimize the building industry’s energy and environmental footprint through refining building design, building modeling, performance optimization, and intelligent controls. He won “Energy Engineer of the Year” in 2000 from the Association of Energy Engineers (AEE). He has held numerous positions within ASHRAE, including chairman of the Chapter Technology Transfer Committee and chairman for Technical, Energy and Governmental Activities. He is a past president of AEE and has instructed the association's certified-energy-manager training course. He is the current chairman for the Building Intelligent Quotient (BIQ) within the Continental Automated Buildings Association (CABA) and also is a member of the Zero Energy Commercial Building Consortium.