Protecting Facility Networks From Cyber Attack
The promise of interoperability long touted by manufacturers of building-automation and industrial control systems became a reality through the use of Internet protocols, but incorrect assumptions have led to serious consequences for systems and buildings.
Using drivers in network controllers or the Extensible Markup Language (XML) layer as translators, disparate protocols from BACnet to LON to OPC and Modbus have been marshaled through Web-based dashboards to offer complete building control from any place with an Internet connection. Recently, researchers discovered shortcomings that make these systems and the buildings they control vulnerable to attack by hackers and other malicious parties. Without appropriate precautions being taken, essentially all elements of a building, including HVAC, thermostats, automated identification- (ID-) card systems, doors, lights, elevators, and even the corporate local area network (LAN), are open to attack and manipulation through a building-automation system (BAS) or an industrial control system (ICS).
BAS and ICS networks relying on Internet Protocol (IP) connectivity for interoperability once were viewed as too unique to be vulnerable. Even if a network were breached, the hacker would be unable to make sense of it, the thinking went. Thus, a philosophy of “security through obscurity” prevailed in the controls industry. The result was networks with weak, default, or nonexistent log-in-credential requirements and limited deployment of firewalls.
For years, information-technology (IT) networks were the primary target of hackers and, thus, the recipient of the lion’s share of network-defense effort. Today, network defense is relatively mature, and hackers are less discriminatory as to entry points to an organization, looking for any weak links that still exist. As a result, control systems are receiving more attention from network-security professionals.
Many wonder: Why would someone attack a control system, and what is the real risk to business and industry? In some cases, hackers may not understand what they have accessed and inadvertently cause damage, creating a significant financial hardship for a company. Or a hacker may intend to damage critical equipment or infrastructure—for example, damage chillers to elevate the temperature in a data center and destroy servers containing crucial information. A more likely scenario is that hackers are looking for a backdoor through which to access a corporate LAN. This could allow them to obtain proprietary company information or steal customer data. Hackers also could take over computers in a network, converting them to botnets used in a large-scale distributed-denial-of-service (DDoS) attack against another company.
Awareness of these threats is growing. The U.S. Department of Homeland Security (DHS) has expressed concern about ICS vulnerabilities and how they could impact water supplies and the power grid. The DHS also is concerned about the security of government buildings and military installations with Internet-connected BAS. Other entities at risk are banks and financial institutions, data centers, and hospitals, which hold large amounts of personal data on computer networks. Meanwhile, oil, gas, and petrochemical processors are vulnerable to sabotage. High-profile companies that are potential targets of hackers are starting to question the security of the automation systems in their buildings.
Recently, a security firm connected a series of fake ICS to the Internet to mimic the ICS/supervisory-control-and-data-acquisition (SCADA) devices used to help run many power and water plants. The objective was to test the vulnerability of the systems. Over a 28-day period, researchers detected 25 sustained attacks from 11 countries. These were not automated attacks targeting any Internet-connected system, but, rather, specific attempts to compromise Internet-facing ICS/SCADA systems, the researchers said.
Today, control systems for all types of buildings and industries have a public IP address that can be accessed by anyone or from any internal corporate IP address. A significant number of these Internet-facing systems are largely unpatched and easily accessible because of faulty password protections.
Older BAS and ICS technologies are especially vulnerable because they were not designed to handle rigorous security measures, such as encryption. Additionally, systems integrators (SI) are not trained in IT-network configuration, and security is not part of a typical BAS service agreement. Furthermore, system patches for older equipment are rare because manufacturers seldom produce a patch for anything other than the latest update of their BAS. Unlike patches for desktop computers, which happen automatically and quickly, patching a control system usually requires a technician/programmer to spend several hours on site. Patching a BAS requires the following of sequences and careful scheduling. Also, the system, including all components and controllers, must be recycled, which, if not handled properly, can cause a BAS to crash. For these reasons, patching control systems likely will remain a highly manual—and expensive—process for many years to come.
Fortunately, there are solutions to the critical issue of BAS and ICS vulnerability. Some work in the short term and need to be implemented immediately to provide protection:
Get behind the wall. Web-facing control systems need to be behind a firewall or virtual private network (VPN), if online access is required. Typically, these customers are using a public IP in the supervisory personal computer (PC). Firewalls and VPN are created to be put on the Internet; supervisory PC and other industry hardware were not.
Implement user-ID/password policies. Often, SI share a single user ID/password companywide so any technician can get into any system for any customer. In such cases, the password should be changed at least periodically and especially after an employee leaves the company. If a system still has the user account of a former employee, perform audits to identify the system, and monitor its use. Remove or change vendor passwords when changing vendors. Lastly, policy must dictate the creation of complex passwords and be strictly enforced.
Educate the on-site workforce. It is not uncommon for members of a facility’s staff to surf the Web using the BAS supervisory PC. Instruct them that this puts the entire system at risk. Also, be sure they adhere to the user-ID/password policy. User-account maintenance needs to be a key part of cyber-security policy.
Thinking long term, additional measures to optimize the safety of a BAS and network can be taken:
Patching. As noted earlier, patching a BAS involves more than a couple of mouse clicks. Beware of the pitfalls: Patching sometimes requires a reboot of the supervisory PC, which could negatively impact downstream field controllers. Also, it could require a full system upgrade. Key to the success of any patching program is careful strategizing:
• Make sure system elements can run in standalone mode.
• Have a clear backout plan.
• Monitor systems to confirm patches are performing as expected.
• Build a test environment, if possible.
Upgrade. The life cycle of an IT system usually is three to five years, while that of a control system often is a decade or more. Thus, while companies typically budget for IT-system replacement, funding rarely is available for BAS replacement. As a result, older systems remain in place, vulnerable to cyber attack. Upgrading sometimes creates problems, but these can be avoided with a well-thought-out process:
• Review the current system for compatibility with the planned upgrade.
• Avoid control-system-sequence interruption.
• Include a backout procedure.
Protect. It may be necessary to restructure a network and associated hardware to provide customer-required functionality while maintaining system and network security. Following are some control-system-network configurations a SI may encounter in the field:
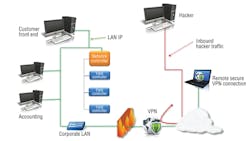
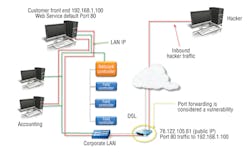
• The control system is set up on an independent LAN and connected to the corporate LAN and possibly the Internet, but protected by corporate IT security measures (Figure 1).
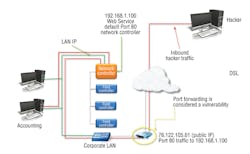
• The control system is not connected to the corporate LAN, but has a digital-subscriber-line (DSL) connection and is accessed remotely using a static public IP or port forwarding from static public IP to private IP (Figure 2).
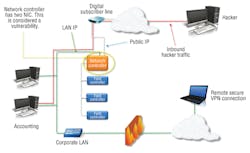
• The control system is connected to the corporate LAN and can be accessed internally using a private IP and externally using a static public IP (Figure 3).
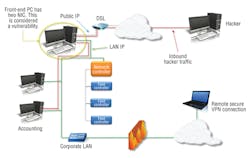
• The control system is connected to the corporate LAN and can be accessed internally using a private IP and externally using port forwarding to a static public IP (Figure 4).
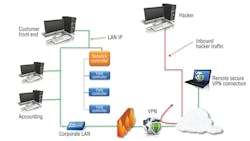
These configurations offer varying levels of security and vulnerability, and none is ideal. The following configurations offer the greatest security and are recommended for customers requiring Internet access for their control systems:
• Control system connected to the corporate LAN and accessible internally using a private IP and externally via a VPN to the private IP (Figure 5).
• Control system connected to the corporate LAN and accessible internally using a private IP and externally using a secure remote control method (Figure 6).
Unlike legacy IT-network professionals, SI are not educated on cyber threats and how an attack can happen, let alone how to prevent an attack. Things SI do routinely and take for granted signal red flags and set off alarms for IT-network professionals. For example:
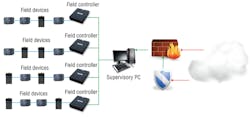
• Suspicious traffic—Information in the BAS goes back and forth between the controller and field devices. To IT-network professionals, this traffic is suspicious and appears to be a threat to their systems.
• Too many chiefs—SI tend to install most control software as “administrator.” IT-network professionals see a relatively large number of administrators as a vulnerability.
Communication between SI and IT staffs throughout BAS projects can resolve these conflicts. When an IT staff understands the purpose of BAS communications, it will not try to shut down the system. Likewise, by implementing strict password control and authentication practices, SI can assure IT staffs that administration computers are protected.
Summary
The threat to BAS and ICS is growing by the day, as would-be attackers learn more about the critical infrastructure these systems control and the systems’ inherent security weaknesses. Owners and operators need to educate their staffs on cyber threats and secure and monitor BAS the same way they do IT systems. SI must recognize the threats posed to the systems they install and maintain, implement security procedures, and make best practices a priority. Fortunately, vendors are developing security programs, and their products are becoming more secure. Although the threats of today likely will persist, and new threats will emerge, with cooperation and communication between all parties, control systems can be secured while still providing the benefits building operators have come to expect.
Mark Balent, president and chief executive officer of LONG Building Technologies in Littleton, Colo., a full-service HVAC representative and building-automation-, security-, energy-, and mechanical-services company, and Fred Gordy, technology evangelist, Enterprise Intelligence Group/ACS, for McKenney’s Inc. in Atlanta, provider of facility-construction, operation, and maintenance solutions, hold leadership positions in InsideIQ Building Automation Alliance, an international organization of independent building-automation contractors. They can be reached at [email protected] and [email protected], respectively.
Did you find this article useful? Send comments and suggestions to Executive Editor Scott Arnold at [email protected].